- Developers
- Developer Blog
- Blockchain Development
- Will Quantum Computing Destroy Bitcoin?

profile

By Aran Davies
Verified Expert
8 years of experience
Aran Davies is a full-stack software development engineer and tech writer with experience in Web and Mobile technologies. He is a tech nomad and has seen it all.
Wondering if quantum computing will destroy bitcoin or blockchain? This is a very interesting question that we will answer here.
With Google claiming to have reached quantum supremacy, the technology of quantum computers may not be very far off.
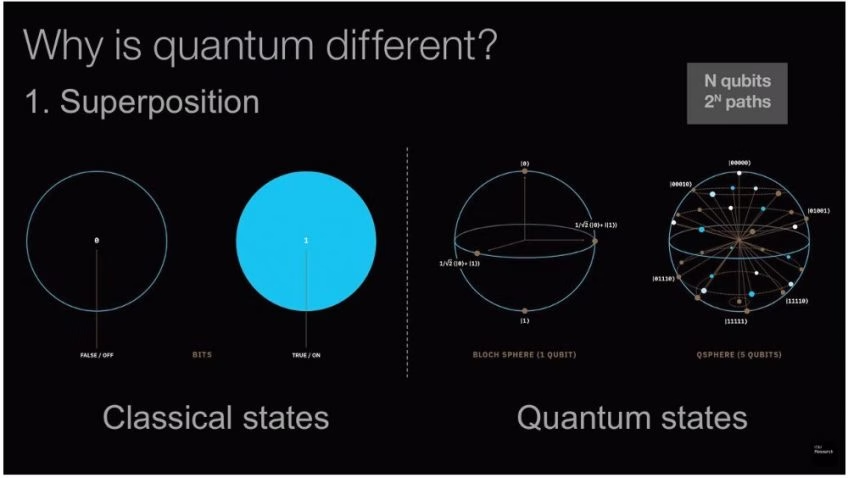
Quantum computers can do what today‘s computers can‘t
You can see that the Bitcoin blockchain achieves the three security objectives because today‘s computers have limited computing ability. This is because the current computing technology uses ’Bits‘, i.e. the smallest unit of storing information.
A ’Bit’ can only have a ’0′ or a ’1′ at any given point in time. The entire gamut of current computing algorithms is built on processing these ’0’s or ’1’s. Read more about ’Bits’, i.e. ’Binary Digits’, in this Computer Hope definition.
However, quantum computing, a technology currently in a research and development phase, doesn’t rely on ’Bits’. It uses ’Qubits’, i.e. ’Quantum Bits’. Qubits can hold a ’0′, a ’1′, and a superimposed state of both, all at the same time.
This creates a completely different computing paradigm, with significantly more computing power than today‘s classical computers. Read about Qubits in this TechTarget Qubit definition.
Before I start the quantum computing vs blockchain debate, I will explain the origin of quantum computing, starting with quantum physics.
Quantum physics gave birth to quantum computing concepts
Hire expert developers for your next project
Quantum theory is a path-breaking theory in physics, and it evolved as follows:
- Physicist Max Planck in 1900 stated that energy has individual units like matters have particles. He named these units ’Quanta‘.
- Albert Einstein in 1905 added to it and declared that radiation also has quantifiable smaller units.
- Louis de Broglie stated in 1924 that at a fundamental level both matter and energy behave similarly, and this theory became known as the ’Principle of wave-particle duality‘.
- In 1927, Werner Heisenberg came up with the ’Uncertainty Principle‘. It states that if we try to precisely measure two complementary values, for e.g. position and momentum, of a subatomic particle, the very act of measurement of one will change the other.
Read this TechTarget definition of quantum theory, for more details.
Quantum computing utilizes the above concepts, i.e. a Qubit can have a ’0′, a ’1′, and a superimposed state of both, all at the same time. Note the application of wave-particle duality principle above. In a short while, I will explain how it also uses the ’Uncertainty principle‘.
Pros of quantum computing
This concept of superimposition frees quantum computers from the confines of linear equations. It can solve exponential equations, and this added processing power allows for significantly faster processing and needs less energy.
In the future, computer scientists will be able to use quantum computing and make massive advances in many fields, for e.g.:
- Chemistry;
- Applied Mathematics;
- Biology;
- Engineering;
- Artificial Intelligence (AI);
- Machine Learning (ML);
- Big Data and Analytics.
Read more about quantum computing uses in “Blockchain and Quantum Computing”.
How quantum computing impacts storing crypto data securely
Private key-public key data encryption secures digital signatures of Bitcoin users. Read our article for more detail. It uses such exceptionally large numbers for prime factorization that classical computers can‘t practically break it.
However, that could change with the quantum computer. Peter Shor had introduced a polynomial-time quantum algorithm in 1995, which we now call ’Shor‘s algorithm‘.
It dramatically demonstrated how the new algorithm requires a very less number of operations to solve a large prime factorization problem, compared to a classical algorithm. In effect, a powerful quantum computer running ’Shor‘s algorithm‘ could solve such a problem in a few days.
Compare this to hundreds of billions of years that classical computers would take to solve a similar problem! Read more about ’Shor‘s algorithm‘ in “Shor‘s algorithm”.
This can put today‘s private key-public key data encryption at risk. Don‘t lose your sleep immediately, though, because quantum computers aren‘t commercialized yet.
However, keep in mind that many organizations are seriously researching and developing this technology. For e.g., Google and IBM are already working on their quantum computers. If you want to read a few examples of their research, check out the IBM Quantum Experience website.
Hire expert developers for your next project
1,200 top developers
us since 2016
Quantum Resistant Ledger: Responding to Will Quantum Computing Destroy Bitcoin Blockchain
Responses to the quantum threat to blockchain are coming up. For e.g., a blockchain project team has created “The Quantum Resistance Ledger” and intends to solve the digital signature-related threat.
The QRL project team implements a set of post-quantum secure data encryption algorithms. It’s called ’eXtended Merkle Signature Scheme’ (XMSS). It uses a ’One Time Signature’ (OTS), where you can sign only one transaction with one key.
This makes hackers with quantum computers irrelevant. There‘s no fixed private key for them to hack from a public key. Instead, the signature changes every time the user signs a new transaction.
The project team claims it’s a peer-reviewed algorithm, and they have launched their Mainnet. Read about their XMSS solution in the FAQ section of the QRL website.
Addressing quantum computing blockchain challenges using quantum key
In May 2017, researchers at the Russian Quantum Center developed a blockchain that they claim is safe from quantum computers. They did it by combining post-quantum cryptography with quantum key distribution (QKD).
In QKD, laser beams transmit cryptographic keys, and they use the quantum properties of photons for this. The photons have their quantum properties coded in binary ’0‘s and ’1‘s.
Remember the ’Uncertainty principle’ that Heisenberg had formulated? The very act of observing subatomic particles’ property changes the property.
When hackers try to intercept the keys in transit, their snooping act changes the quantum properties, and makes those keys unusable! Read this techopedia definition of QKD for a deeper understanding of it.
Incidentally, QKD networks are already in use, to manage smart contracts. There are several such networks in the US, Europe, and China already functional. Read more about it in “Russian researchers develop ‘quantum-safe’ blockchain”.
Quantum entanglement computing for blockchain quantum computing “marriage”
Two researchers from the Victoria University of Wellington, New Zealand, suggest that blockchain can move beyond just using quantum cryptography. They propose quantum entanglement computing to create a new type of blockchain.
They propose to use the entanglement concept from the quantum physics for this. Two entangled quantum particles share their existence, at a point in space and time when they interact with each other. From that point onwards, if you try to measure one, it will influence the other.
Hire expert developers for your next project
Del Rajan and Matt Visser, i.e. the two researchers plan to use this property. They plan to create blockchain where one quantum particle will encode the history of all its‘ predecessors. This follows that if our hackers try to hack a predecessor particle, their snooping act will destroy that particle.
This quantum networked blockchain will survive, though! Remember that the last particle in this blockchain has all predecessor particles‘ in it! Read about their proposal in “If quantum computers threaten blockchains, quantum blockchains could be the defense”.
Blockchain communities need to be proactive
It‘s clear that quantum computers will take some years before a commercial version comes in the market. Hence, blockchain networks and data encryption might be safe now. However, the blockchain ecosystem shouldn‘t underestimate the threat.
As you know, blockchain has attracted a lot of interest, and we may see many businesses and governments adopting it aggressively. Now, consider the impact of a sudden release of quantum computers, which will significantly reduce the security of blockchain immediately.
By that time, businesses, governments, and communities will have invested significant energy and resources to adopt blockchain. They will suddenly find that their investment doesn’t count for much! To avoid such an unpleasant scenario, blockchain communities should proactively address the threat of quantum computing.
Interested in Blockchain Application Development?
Despite the growing security concerns, businesses are adopting blockchain technology increasingly. According to a study, “The global blockchain market size is expected to grow from USD 3.0 billion in 2020 to USD 39.7 billion by 2025”.
If you, as a business CEO or CTO, are looking to partner with an experienced software development company for your blockchain project, DevTeam.Space can help you. Write to us your initial blockchain development and security requirements through this form and one of our technical manager will match you with expert blockchain developers.
Frequently Asked Questions on Will Quantum Computing Destroy Bitcoin
A large enough quantum computer can potentially execute complex algorithms incredibly faster than a current classical computer. A big enough quantum computer can potentially break the encryption technology used in blockchain. These quantum attacks might help an individual to hijack blockchain networks. However, blockchain networks don’t face an immediate threat from quantum technologies.
In the future, quantum attacks might be able to break the encryption algorithms used in Bitcoin. However, quantum computers can’t do that yet. There’s likely a 5-10 years window for Bitcoin to strengthen its security measures so that it can survive hackers armed with quantum computers.
Some cryptocurrencies have anticipated the threat from quantum revolution early. They have worked on building quantum-resistant blockchain networks. A few examples are QRL, Hcash, and IOTA.

Alexey Semeney
Founder of DevTeam.Space
Hire Alexey and His Team
To Build a Great Product
Alexey is the founder of DevTeam.Space. He is award nominee among TOP 26 mentors of FI's 'Global Startup Mentor Awards'.
Hire Expert Developers