Drupal Security: How to Protect Your Website?
Have you come across Drupal Security and are wondering how to protect your app?
You've come to the right place.
Every few days hacking incidents are reported around the world; some incidents are innocuous whereas others can be more serious and result in the loss of personal, financial, or consumer data.
As an owner of the website, there is nothing more petrifying than the thought of having all your work changed or completely wiped off by malicious users or software.
Hackers, spammers, thieves, and intruders are constantly on the lookout for data that can easily be exploited. Hacking is one of the greatest threats posed to businesses in the online world so why not spare some time to protect your website against such exploits.
In this blog post, this is exactly what we explore. In particular, we focus on Drupal from a security perspective, and whether you‘re a web developer technical lead, involved in server maintenance, or even considering implementing Drupal for the first time after you‘ve read this blog post, you‘ll have an in-depth understanding of Drupal, how to protect it from malicious users and keep your data safe.
How Vulnerable is Drupal?
Have you ever thought about the risk you're at when it comes to Drupal? Well, according to the Common Vulnerabilities and Exposure (which is an online vulnerability source of data) there have been more than 290 vulnerabilities reported since 2002.
Drilling into this data a little more closely reveals that 46% of Drupal vulnerabilities are caused by cross-site scripting. Here is the breakup:
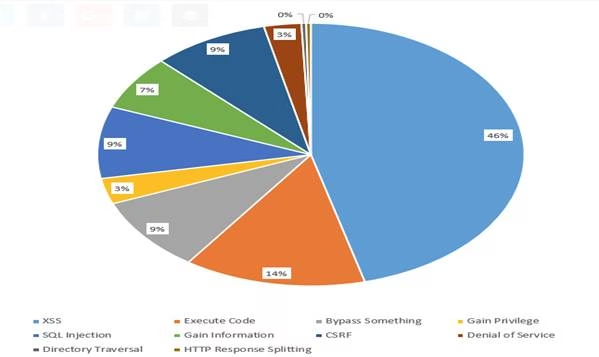
Source: (Jackson, 2018)
Security Features and Differentiating Factors
Drupal is a content management system and powers approximately 2.5% of all websites. It is an open-source system written in PHP and sets itself apart from the competition by providing regular updates that result in more features and enhanced security.
There is a large Drupal community of developers that continually contribute to enhance drupal security modules and themes in the Drupal ecosystem and has been developed with security in mind to ensure that websites built on the platform are safe and secure.
That said, outdated Drupal systems can be at risk from vulnerabilities making it essential to follow the best practices of security. Securing your Drupal-based website is only possible if you understand how security features work in Drupal, some of which we will discuss next.
Drupal security features
Some of the Dupral security features include:
Secured Access
Passwords for Drupal accounts are strongly encrypted when they are stored in the database and can aid a wide range of policies associated with the creation of passwords including expiry, the minimum character count, and the level of complexity.
2-factor authentication and SSL also support various industry authentication practices. This authentication keeps unauthorized crawlers away from your website.
Granular Access Control
With Drupal, administrators can have greater control over who can view and who can make changes to every part of the site. The software operates on a system of user roles and access permissions.
This allows administrators to create roles that give limited permission to the viewers. For example, a site might create an Author role that permits him or her to update the content but will not have the authority to publish or remove any content.
When compared to the other popular content management systems, Drupal proves to be protected from the most common malware. Drupal offers a flexibility feature with the presence of multiple attractive themes and customization options for you to choose from.
Managing updates with the Drupal Update Manager
For any content management system, software updates or patches are vital. Every new update is aimed at resolving the issues faced by the older version. New updates also provide enhanced security and the ability to fix bugs.
Drupal ships with the ’Update Manager‘ which is a unique module that tracks the latest updates for you. It automatically notifies about new themes and modules to your Drupal-based website. Considering the nature of the module, this is a must-have feature for your site.
Modules to further improve your Drupal security
Consider the following modules to improve the security of Drupal sites.
Login Form Module
This Drupal module provides security in your Drupal login forms. Login forms are a common practice for a lot of public-facing websites. Drupal implements common patterns such as:
- limiting the number of failed login attempts;
- restricting access by IP address;
- hiding the reason for login failure, thereby making it difficult for the attacker to find out if the account exists or not;
- provide notifications of any efforts that can threaten the security of the website.
Password Policies
This module is used to provide constraints during password creation that ensure the strength of the password.
The use of capital letters, special characters, numbers, and a specific length is necessary. It does not allow the creation of two similar passwords and automatically sends the notification for password renewal after a certain period.
Captcha
Another challenge is to protect the website from spambots. Drupal makes it easy to detect if visitors of your site are human or not. By implementing CAPTCHA, your Drupal site blocks any automated scripts and prevents flooding of your back-end database or mail server.
Flood Control
Hackers have been recently using Brute forcing to crack even the most robust passwords. It works like the other module and protects Flood Control by limited login attempts.
Hijack Prevention
This module is used to provide a little extra protection to pages that are already secure and prevents the hijacking of SSL pages on your site. This module should be used for even the most secured pages on your website.
Timeout
This module is particularly crucial for the security of your website as it lets you set the expiry time of an idle session. It can be adjusted based on the roles of the drupal users, and in some cases, the users are allowed to set their own time to ensure the security of user accounts.
Concurrent Sessions
This module makes sure that a single user cannot use multiple sessions. It only provides one session for one browser. A new session, on the same browser, can only be used upon logging out from the previous session. This provides an extra security layer to the website and protection of the accounts.
Access to Content
This module helps you set the limit to the entrance of a particular user or role. Permissions can be applied to the use, editing, and removal of the content. The initial module has a default-setting feature that can be altered as per the requirement of the said user.
Tips for securing your Drupal website
Now that we‘ve discussed what is drupal, what are some of the security modules, and have explored some of the most common security vulnerabilities that Drupal has, it‘s time to turn our attention to some tips we‘ve gathered that will help you tighten up security for your Drupal implementation!
Update to the latest Drupal Version
If you are an existing Drupal user, updating your software to Drupal 8 is the first step you need to take. Take time to carry out some smoke testing after you‘ve performed you're upgrading, for example, clicking on buttons that perform common tasks and making sure your site doesn‘t error.
Verify that database interactivity is operational and if you send emails from your site, validate that email can still be relayed over SMTP.
Upgrading Drupal will not only provide you with some exciting new features but advanced security fixes that help enhance your website performance and security.
Up-to-date Modules
Upgrading to the latest version of Drupal is not enough to save you from security risks. Make sure your Drupal modules are also up-to-date. By ensuring that all your existing modules or Drupal core code are up-to-date, you can greatly lessen the risk of your site being exploited.
Websites or scripts that run outdated modules can be easily exploited by hackers. Using updated versions will not only bring new features but also provide bug fixes and other security measures. Keeping on top of updates ensure that your website is free from known vulnerabilities.
Choosing Selective Modules
Drupal gives you the opportunity to customize your website using thousands of modules. It is important for you to extend the capabilities of your website while making sure that is not compromised at the cost of security. Only install modules that you absolutely need!
Safety against Malicious Files
If you give users the option to upload documents to your Drupal site and don‘t monitor the types of files they can upload, hackers can upload malicious scripts or viruses that can wreak havoc on your site without your knowledge.
This type of problem can be easily solved with Drupal‘s in-built allowable “Content-Type” security. You can make changes by performing the following steps:
- Go to “Structure > Content types > Manage Fields”, and Click “Edit” next to Images to remove the image files types.
- To allow uploads such as PDFs, go to “Administer > Site Configuration > File Uploads”. Remove HTML and script files from the permitted file extensions.
- Click Save.
Handle dangerous HTML with “htmLawed”
Malicious users or hackers can compromise your website by uploading dangerous HTML. One module you can use to sanitize HTML that users upload is ’htmlLawed‘.
The module allows to define policies and standards for security and offers rich configurable options in terms of the types of HTML that users can use in your Drupal site. Download and install this module to add another layer of security to your Drupal implementation.
Duo Security - Two-Factor Authentication Module
Two-step verification can strengthen your Drupal website by forcing users to supply two methods (or factors) of information that verify their identity.
Using a two-step verification gives an extra layer of security to your website and enabling this module ensures the person accessing your Drupal site is who they say they are.
Users can supply a username and password combination and are forced to supply a token or unique ID from something like a smartphone application to approve authentication requests.
You can learn more about this module and download it from here: https://www.drupal.org/project/duo.
Paranoia Module
This module seeks to identify all the places that a user can evaluate PHP scripts through Drupal‘s web interface and then blocks those and contains the following features:
- Disable providing the “Use PHP for block visibility” permission;
- Disable making changes to the user# 1 account;
- Avoids giving risky permissions;
- Disables the creation of PHP formats that use the PHP filter.
The Paranoia Module provides additional security to Drupal by reducing the possibility of hackers being able to grant themselves elevated permissions on your site.
Find out more about this module here.
Finally
After you‘ve installed and configured some of the modules that we‘ve just discussed, take the time to do an audit of your existing infrastructure, password policies, and database backup schedules.
In this section, we‘ve pulled together some final tips, and whilst not all of them will be Drupal specific, they are certain ideas that you should consider implementing to further improve the security of your Drupal website.
Use Complex Passwords
Enforce a password policy for your Drupal site with strong usernames and passwords. Choosing a complex password acts as a protective layer that saves your website from hackers.
Hackers can create bots that operate 24x7, that constantly attempt to crawl the internet and find security loopholes such as brute-forcing login attempts with default admin passwords. You can mitigate this risk by implementing a password policy that mandates the use of complex passwords.
Make Use of Secured Connections
Make sure that the connections you are using are secure no matter where you are working. You should make use of the “SFTP encryption” (Secure FTP).
Note: A few FTP clients save encoded passwords on your systems. Some encoded passwords can be converted back to their original form. It is recommended that the users do not save FTP passwords in the clients or avoid setting up master passwords.
It is also important to ensure that the firewall rules are set up at home and on your routers. Note that these are not trusted networks while working in a public place.
HTTPS and SSL certificates
This needs to be configured on e-commerce or any other website which contains critical or sensitive data. SSL or Secure Sockets Layer, to give its full name, helps encrypt communication between the user‘s web browser and your Drupal website.
You might not think that you need to encrypt blog posts or content on your Drupal site and you might have a point, that said, you might be considering installing an e-commerce module such as Drupal Commerce, and if this is the case, you most certainly should install an SSL certificate on your Drupal site.
Planning for the Worst Situation with Backup and Migrate
Would you want your data to be exploited by hackers? Of course not! It‘s important to plan for the worst possible situation however and performing regular database backups should form part of this strategy.
If your database is compromised or worse, completely erased, providing you have regular backups, you‘ll be able to get your site back online with minimal data loss.
"Back up and Migrate” is a module that helps you to create and restore data backups with relative ease and supports archiving formats such as gzip, bzip, and zip.
The module lets you back up all or some database tables to a file you can download or onto a server if you wish. Backup schedules are also available in the module to help you put some of this on autopilot.
Restrict Access to important files on your web server
Another security mechanism you can deploy is to restrict or block access to important files on your web server via the “.htaccess” configuration file.
This is a file that you can edit with fine-grained commands that tell your Drupal implementation how to handle specific types of files and the commands that can be executed against them such as granting or denying access.
The commands in your .htaccess file affect the contents of the directory in which this file is created in. This means that you can create multiple instances of .htaccess to suit your security requirements on a per-directory basis. Consider the following example .htaccess file:
<FilesMatch "(robots.txt)$">
Order allow,deny
Allow from all
</FilesMatch>
This tells Drupal to grant access to the robots.txt file to ALL website visitors which is critical for all websites as you don‘t want to deny access to that!
Alternatively, you may wish to deny access to specific configuration files except to admin users that are on the web server locally. A command similar to the following can achieve this:
<FilesMatch "(xmlrpc.php|install.php|bbcron.php|cron.php|update.php|.txt)$">
Order deny,allow
Deny from all
Allow from 127.0.0.1
Allow from 123.123.123.123
</FilesMatch>
Un-necessary modules and access points
Only install modules that you plan on running on your Drupal site. Having fewer functionality or modules on your site means you ultimately have fewer things to protect against security vulnerabilities. If there is a module that is not needed by you, then remove it.
Another precaution you might want to consider is to restrict administrator access to your Drupal site based on the user's IP address.
The majority of businesses have static IP addresses that sit within a particular subnet or range, consider restricting logins to your Drupal Admin console based on a particular range of IP addresses. If employees need to access the admin console externally, you may also want to consider a VPN.
Sensible User Access
You might have multiple logins to your site, if so, determine the types of roles and associated permissions that each user should have.
Implement a “least privilege” policy to ensure that users only have permission to execute functionality that is needed for their set of responsibilities.
For example, if a colleague is tasked with writing blog posts, ensure that their account does not have complete administrator privileges. The account of your colleague should only allow him or her to create or edit blogs and there is no need for them to have access to updating administrative settings within your Drupal site.
Having carefully defined access will reduce any mistakes that can be made and limit the damage that can be done by the “rogue “users.
Remove Hidden Backdoors
Hackers try their best to find a way to enter your website. There can be multiple numbers of backdoors of various types that can be easily exploited by them. These backdoors can be in the form of legitimate files within the official Drupal framework but located in the wrong directories.
Attackers can inject software such as viruses via backdoors and directories like “/modules, /themes, /sites/all/modules, and /sites/all/themes”.
Common PHP functions where backdoors can be injected include, but are not limited to the following:
- str_rot13
- gzuncompress
- gzinflate
- eval
- exec
- create_function
- href
- curl_exec
- stream
Identify if you have any potential security flaws or patches that need to be installed for any of the above to help mitigate this risk.
Check your sources
When selecting a Drupal theme or module, spend some time to verify that the company or developer that has written said theme/module is professional.
Only select modules that are being maintained and supported regularly and that meet your requirements. Do not download random themes that are available on the internet. Only use choose those themes that belong to Drupal‘s Download and Extend library and which have been maintained recently.
Summing up Drupal Security
So, there you have it, how to protect your Drupal website. In this article, we‘ve explored just how vulnerable Drupal can be, what some of its existing security features are, and detailed some tips that show you how to best safeguard your Drupal website.
We hope that by reading this article you‘ve gained some valuable insights and tips in terms of how your Drupal security team can protect your Drupal website against unscrupulous hackers.
Feel free to share or comment on this article. Are you using Drupal in your business? What security measures have you implemented?
If you need experienced software developers to ensure robust and secure software development and deployment, partner with competent and expert software developers. If you do not find such developers in your project team, contact DevTeam.Space.
You can easily outsource field-expert software developers by writing to us your initial project specifications. One of our account managers will get back to you with more details.
References
Jackson, B. (2018). Complete Guide on Drupal Security. KeyCDN Blog. Retrieved 2 February 2018, from https://www.keycdn.com/blog/drupal-security/
Frequently Asked Questions on Drupal security
There are a variety of methods and applications that can help you protect your website from attack. One example is Drupal, which is a much-loved security application. Ensuring that your developers write bug-free Drupal code is another example.
You need to enable the update manager module before navigating to /admin/reports/status. You will then be told if there are any new updates which you can then choose to install.
You need to get an (SSL) CERTIFICATE, configure the server, enable SSL, and then complete the installation.