- Developers
- Developer Blog
- Blockchain Development
- What Are the Benefits of Blockchain Identity Management

profile

By Aran Davies
Verified Expert
8 years of experience
Aran Davies is a full-stack software development engineer and tech writer with experience in Web and Mobile technologies. He is a tech nomad and has seen it all.
What are the benefits of a blockchain identity management system?
Blockchain is a very powerful technology, provided that it is used in the right way. In this article, we will look at the top benefits of blockchain identity management solutions. Let’s start.
Benefits of Blockchain Identity Management Solutions
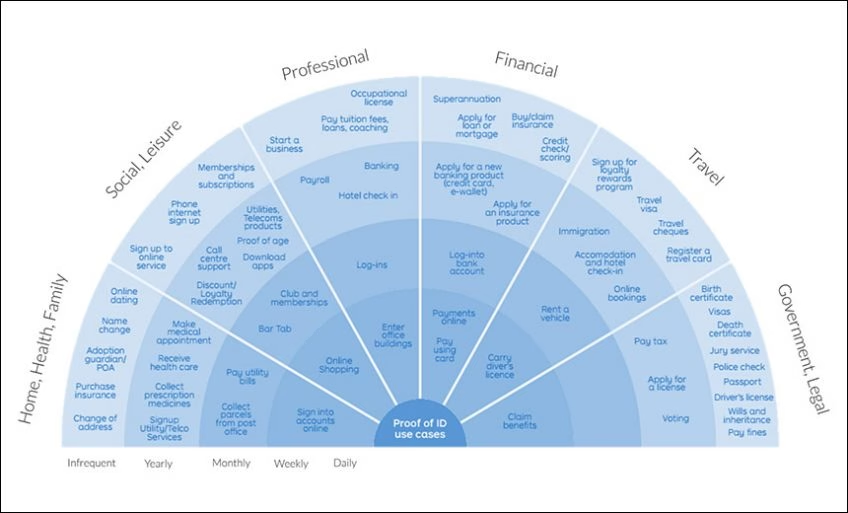
Blockchain digital identity solutions can take several forms, as follows:
1. Ease of obtaining duplicate ID proof after losing the original
This is arguably the easiest application of blockchain technology for digital identity management. As I have already explained, one commonly comes across people that have misplaced their original ID proof document. This results in the following:
- They must go to the relevant government department to get their duplicate ID proof, however, the process is cumbersome.
- Government authorities often have silos of information and manual processes. This delays the issuance of the duplicate ID.
- Underprivileged people such as the homeless, or those living far away from government service centers are the worst affected by this system.
- People living in remote areas may need to visit government offices multiple times to get their duplicate ID proof, due to the multiple-stage process.
Blockchain enables permanence and tamper-proofing of records, therefore, the technology can help here. Government departments can store the individuals’ ID proof on a blockchain. The tamper-proof nature of this record means it is completely safe and reliable, while the security features of blockchain ensure permanence.
In the unfortunate event that someone loses the original ID proof, government officials can easily issue a duplicate ID proof. Read more about this use case in “The impact of digital identity”.
2. “Self Sovereign Identity” (SSI)
The Facebook/Cambridge Analytics data scandal has shown how technology giants like Facebook and Google control and manage users’ digital identities, and how risky this can be. Identity management is complex and due to conventional systems, it is not easy for internet users to manage their own digital identities.
“Self Sovereign Identity” (SSI) can help as follows:

Get a complimentary discovery call and a free ballpark estimate for your project
Trusted by 100x of startups and companies like
- The user owns and fully controls his/her digital identity.
- Other parties can access this identity information, but only with the consent of the primary user.
- By its very design, an SSI is trustless, i.e., there is no need to trust a 3rd party provider.
- SSIs are permanent, therefore, hackers can’t destroy them.
- Their portable nature is a big advantage.
Read more about SSI in “Evernym – private Sovrin self-sovereign digital identity blockchain?”.
Blockchain can help in creating a system where users can obtain their SSIs. In fact, Hyperledger Indy, an enterprise blockchain framework from Hyperledger Consortium caters to digital identity use cases.
Evernym, a blockchain start-up has created a blockchain-powered platform for SSI, and it’s called Sovrin. They collaborate with Indy. I have earlier explained how to create SSI using Indy in “How to build a self-sovereign identity wallet?”.
3. Identity verification using blockchain
As I have explained earlier in this article, implementing an ID management solution can be tricky, in view of silos and the predominance of manual processes. However, the good news is that blockchain start-ups are now offering identity management solutions.
An example is Blockpass, a blockchain start-up offering an identity management solution. Their solution works as follows:
- Blockpass has a “Know Your Customer” (KYC) portal, which is powered by blockchain. This ID verification portal is called “Blockpass KYC Connect”.
- Businesses working in regulated industries must follow stringent KYC regulations, and this portal helps with it.
- Organizations can use this portal for their user onboarding.
- This platform uses smart contracts for KYC and “Anti Money Laundering” (AML) compliance. If you need to learn more about smart contracts, you can read our guide “How to deploy smart contract on Ethereum?”.
- The company provides easy-to-install tools.
- Businesses can use their “Software Development Kits” (SDKs) to integrate Blockpass services with their current systems.
- This platform uses an ERC20-compliant crypto token, and it’s called “PASS”.
- The portal offers shared services, which businesses can use for their user onboarding and other ID management purposes.
While Blockpass is a good example, entrepreneurs can use blockchain platforms like Ethereum and develop their own “Decentralized Apps” (DApps) for ID management.
DApps are like web apps, however, they are open-source, use crypto tokens, run smart contracts as their backend, and run on a decentralized blockchain. I explained this in “How to build an identification app using blockchain?”.
4. Non-custodial login solutions using blockchain
Whether signing into your employer’s networks or logging into an internet-based service, you trust a 3rd party to keep your ID and password safe. The employer or the other service provider maintains central servers to keep your credentials safe.
We call these “Custodial login solutions”. As with any central server, these are also vulnerable to being hacked. In fact, central servers are lucrative targets for hackers, and such incidents of hacking are common.
Blockchain can transform this with its decentralization and enhanced security features. Blockchain-based solutions no longer use central servers, rather they are decentralized and use public-and-private keychains for login.
The employer or the 3rd party service provider can consume these services, with the assurance that only trusted individuals are logging into their systems. An example of such a non-custodial login provider is Remme.
Remme has an open-source distributed protocol for “Public Key Infrastructure” (PKI). It’s a decentralized network, therefore, providers of internet-based services need not store a large volume of user IDs and passwords.
Hire expert developers for your next project
1,200 top developers
us since 2016
Remme uses the following components:
- Masternodes: These handle user registration, ID revocation, etc.
- Hyperledger Sawtooth: This is an enterprise blockchain framework from Hyperledger Consortium.
- “Proof of Service” consensus algorithm: This is for transaction validation.
- REM crypto token: This is an ERC20-compliant token.
Read more about Remme here.
5. Identity management for the decentralized web
Various 3rd party services track every online activity by users. For e.g., “Internet Service Providers” (ISPs) track every site users visit, and 3rd party email tracking services monitor emails. This is possible only because they have the user’s personal information, such as their digital identity.
Increasingly, internet users are looking for a decentralized web, where they don’t need to part with their personal information to access services. However, this requires an appropriate digital identity management solution.
Users should be able to use one digital identity to validate their activity anywhere on the internet. Moreover, they should not have to provide it to every internet-based service provider.
Blockchain can help here. Users can store their digital ID on a blockchain network, and internet-based service providers can access that for user authentication purposes.
Metadium is a blockchain start-up that uses SSI to achieve this. They use a blockchain that lets users create their SSIs. They have a public identity blockchain platform, their “Meta ID” protocol for 3rd party developers, and a DApp named “Keepin”.
6. Managing user identity for “Internet of Things” (IoT) systems
Whether smart appliances, fitness trackers, or remote patient monitoring (RMP) systems, the “Internet of Things” (IoT) is entering our life rapidly. All IoT-enabled devices collect data and stream it to the relevant service providers.
IoT as such does not need any introduction. Billions of IoT-enabled devices already stream valuable data, and many more billions will soon be IoT-enabled. However, all communications from IoT-enabled devices happen over the Internet.
This is a security risk, and if the devices collect sensitive data such as “Protected Health Information” (PHI) then the users are at serious risk. Users must have full control regarding how the data from IoT devices are used. Read more about this in “Blockchain for identity management: 7 possible use cases”.
Identity management for IoT devices should ensure that the data collected by the IoT devices is under the full control of users. Such ID management should also be secure enough to prevent hackers from accessing sensitive information in transit over the internet.
Hire expert developers for your next project
UniqueID is a blockchain project that addresses this use case. They have a distributed ledger for device IDs. Users don’t need to depend on 3rd parties since the platform doesn’t require CA-signed certificates. Users are in full control of their digital IDs.
Have a Great Blockchain Digital Identity Solution Idea?
Blockchain and identity management have enormous potential, however, the solutions are still evolving. Platforms, frameworks, and tools are undergoing significant changes to address scalability and transaction throughput, for example.
An Allied Market Research report projects that this market is growing significantly. The report states that the market for blockchain identity management solutions was valued at $107 million in 2018, however, it will reach $11.46 billion in 2026.
According to this report, banks, healthcare organizations, retail businesses, etc. will realize significant value from blockchain identity management solutions. Not surprisingly, this report projects an impressive CAGR of 79.2% between 2019 and 2026.
Before you undertake a development project, you need the appropriate architecture and industry expertise. I recommend that you engage a reputed software development company for your project. Read “What to plan for when undertaking blockchain software development?” to learn more.
If you are planning to gauge the benefits of blockchain identity management solutions, partner with a professional software development company that knows the technologies, tools, etc.
You can get in touch with DevTeam.Space for blockchain identity management development project via this quick form and partner with our blockchain-expert software developers community.
Frequently Asked Questions on Benefits of Blockchain Identity Management
This refers to a blockchain-based identity management solution. Examples include blockchain-based passports and driving licenses or simply a universal blockchain-based solution to confirm your ID to any third party.
For an identity management system, firstly, you will need to develop a blockchain solution that can be quickly accessed to confirm a person’s identity. Such a solution might interact with hardware for personally identifiable information such as fingerprint or iris scanners. Once you have done this, you will need a secure way to ensure people give the correct information. Then the solution will be able to confirm a person’s identity as and when required. This system protects from identity theft and ensures data security.
Due to the immutability of blockchain records and distributed ledger technology, they are a much better solution for identity and access management than current digital solutions. It seems certain that within a decade, a universal blockchain-based ID solution will be available to confirm identity owners and other digital identity credentials anywhere.

Alexey Semeney
Founder of DevTeam.Space
Hire Alexey and His Team To Build a Great Product
Alexey is the founder of DevTeam.Space. He is award nominee among TOP 26 mentors of FI's 'Global Startup Mentor Awards'.
Alexey is Expert Startup Review Panel member and advices the oldest angel investment group in Silicon Valley on products investment deals.